Securing Agentic AI Systems
As agentic AI systems become more prevalent and powerful, the need for robust security frameworks is critical. Autonomous systems require specialized approaches to risk mitigation. AI systems with complex memory structures require careful controls around how information is stored, accessed, and modified
- Implement trust boundaries between different types and scopes of memory
- Develop structures for live monitoring of memory contents
- Control which components can read or write to which memory elements
- Enable user modification of memory elements when appropriate
- Create pathways for effective remediation of memory poisoning events
- Grant minimum necessary access to limit memory leakage or poisoning risks
**Memory hardening prevents a compromised memory space from cascading into systemic failures.
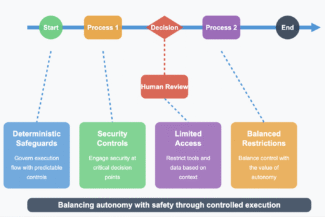 While autonomy is a core feature of agentic systems, unregulated access to capabilities creates significant vulnerabilities: noooo we don’t want these.
While autonomy is a core feature of agentic systems, unregulated access to capabilities creates significant vulnerabilities: noooo we don’t want these.
- Deploy deterministic safeguards that govern the flow of execution
- Scope security controls that engage at critical decision points
- Limit access to tools and data based on contextual appropriateness
- Balance restriction with the value proposition of autonomy
- Create checkpoints for human review of critical operations (always this)
**Thoughtful control flow implementation preserves functionality while reducing risk surfaces.
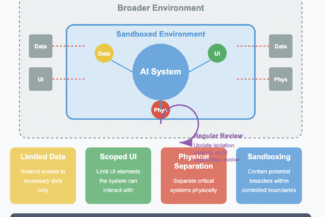 Agentic AI systems interact with their environments, whether organizational, technical, or physical:Limit data accessibility to what’s necessary for intended functions
Agentic AI systems interact with their environments, whether organizational, technical, or physical:Limit data accessibility to what’s necessary for intended functions
- Scope UI elements the system can interact with
- Consider physical separation when appropriate
- Implement “sandboxing” to contain potential breaches (whose your daddy?!)
- Regularly review and update isolation controls as capabilities evolve - best practices win
**Proper environment isolation prevents unintended consequences from spreading beyond controlled boundaries.
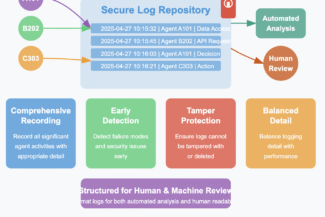 Full activity logs create the foundation for transparency, security monitoring, and effective oversight:
+Record all significant agent activities with appropriate detail
Full activity logs create the foundation for transparency, security monitoring, and effective oversight:
+Record all significant agent activities with appropriate detail
- Design logging systems that facilitate early detection of failure modes
- Ensure logs cannot be tampered with or deleted
- Balance logging detail with performance considerations
- Structure logs to facilitate both automated and human review
**Robust logging transforms invisible AI operations into traceable, analyzable events.
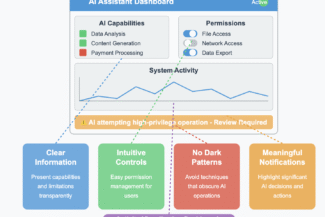 User UI plays a critical role in AI security by facilitating informed consent and meaningful human oversight: Your AI UI matters
User UI plays a critical role in AI security by facilitating informed consent and meaningful human oversight: Your AI UI matters
- Present clear information about AI capabilities + limitations, some call this disclosure
- Provide intuitive controls for managing AI permissions, why is this so hard?
- Avoid dark UI patterns that obscure AI operations, be better
- Design notifications that highlight significant AI decisions
- Create dashboards that visualize system activities
** Thoughtfully designed UX bridges the gap between complex AI operations and human understanding.